JNCTF2025WP
JNCTF2025 WP
————Sally
PWN
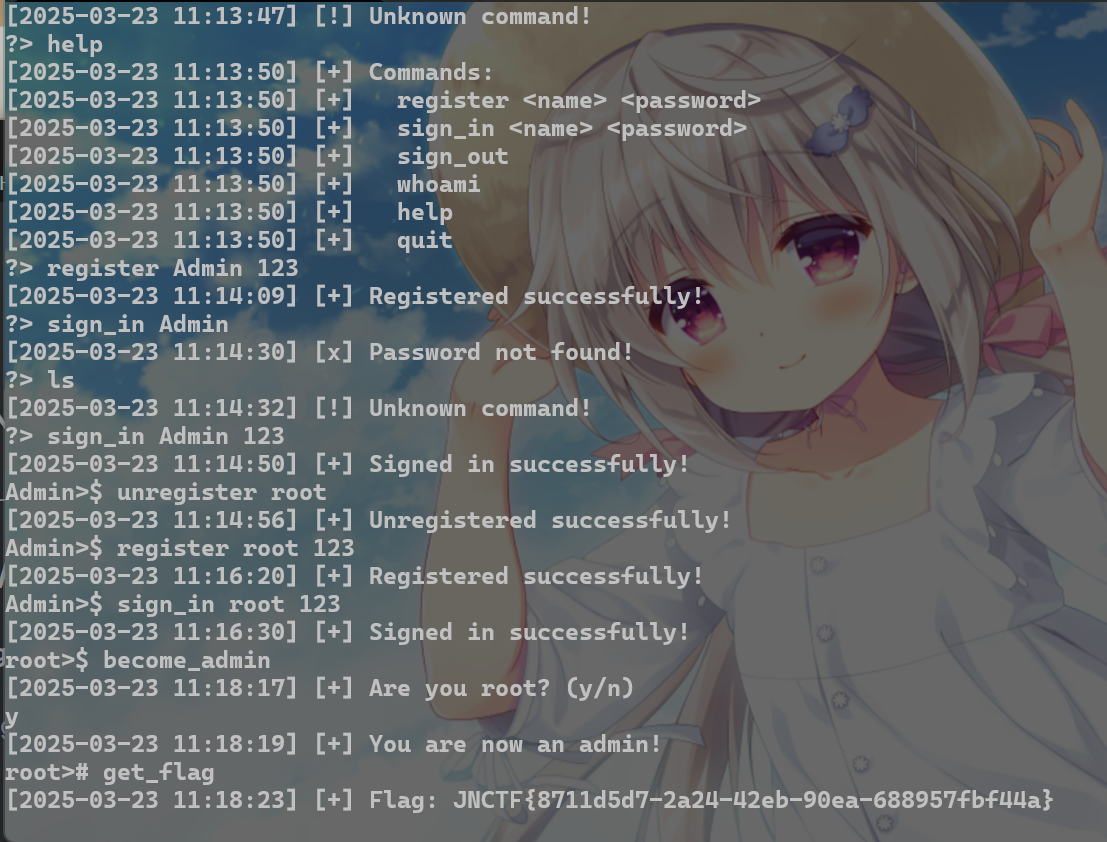
1. signin
unregister的权限问题,可以用Admin账户去注销root账户,然后重新注册root账户就能拿到管理员权限
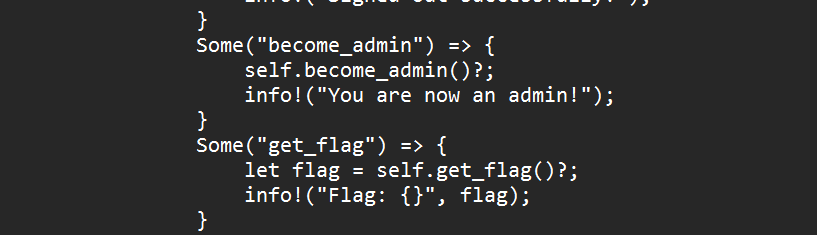
2. shellcoe_master(非预期解法)
这个题给了个沙箱,限制只能用orw,而且write一次只能输出一个字节,还开了PIE保护
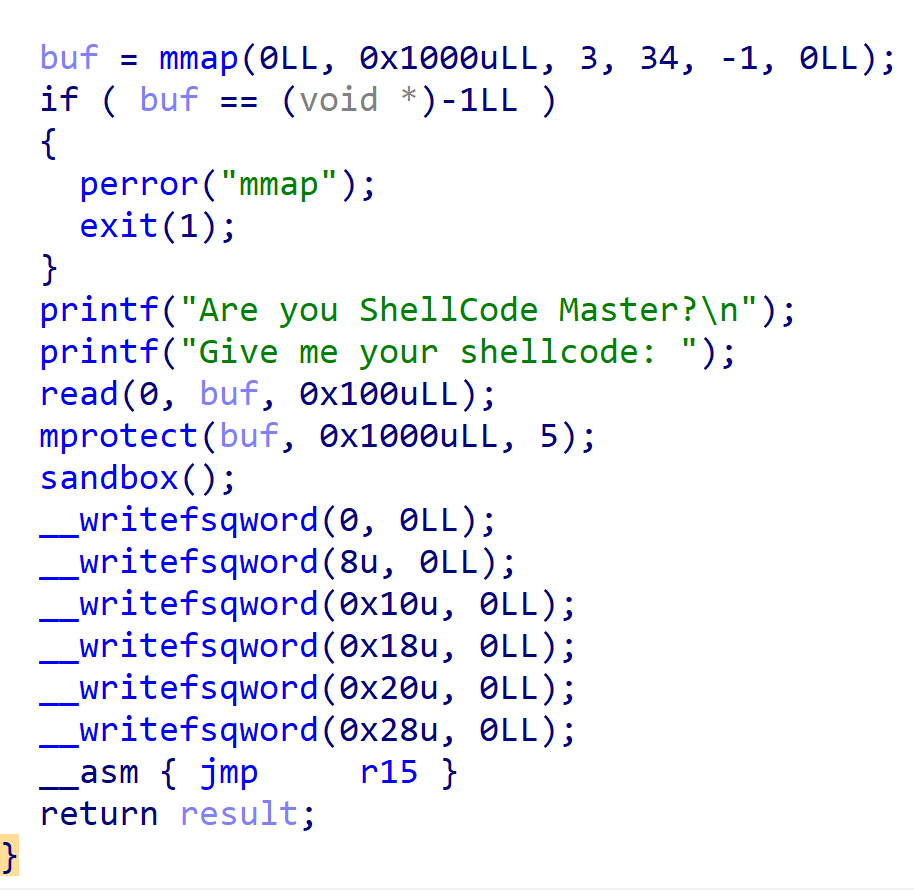
在执行shellcode之前,除r15和rip之外的寄存器全部清0(指向buf的位置)。而且在执行shellcode的时候buf段不可写,也代表着push和pop之类的指令不能用了。
然后想到bss段rw权限,直接把flag写在bss段,然后orw,一个个字节读出来就好了
1 | |
3. shellcode_master_revenge
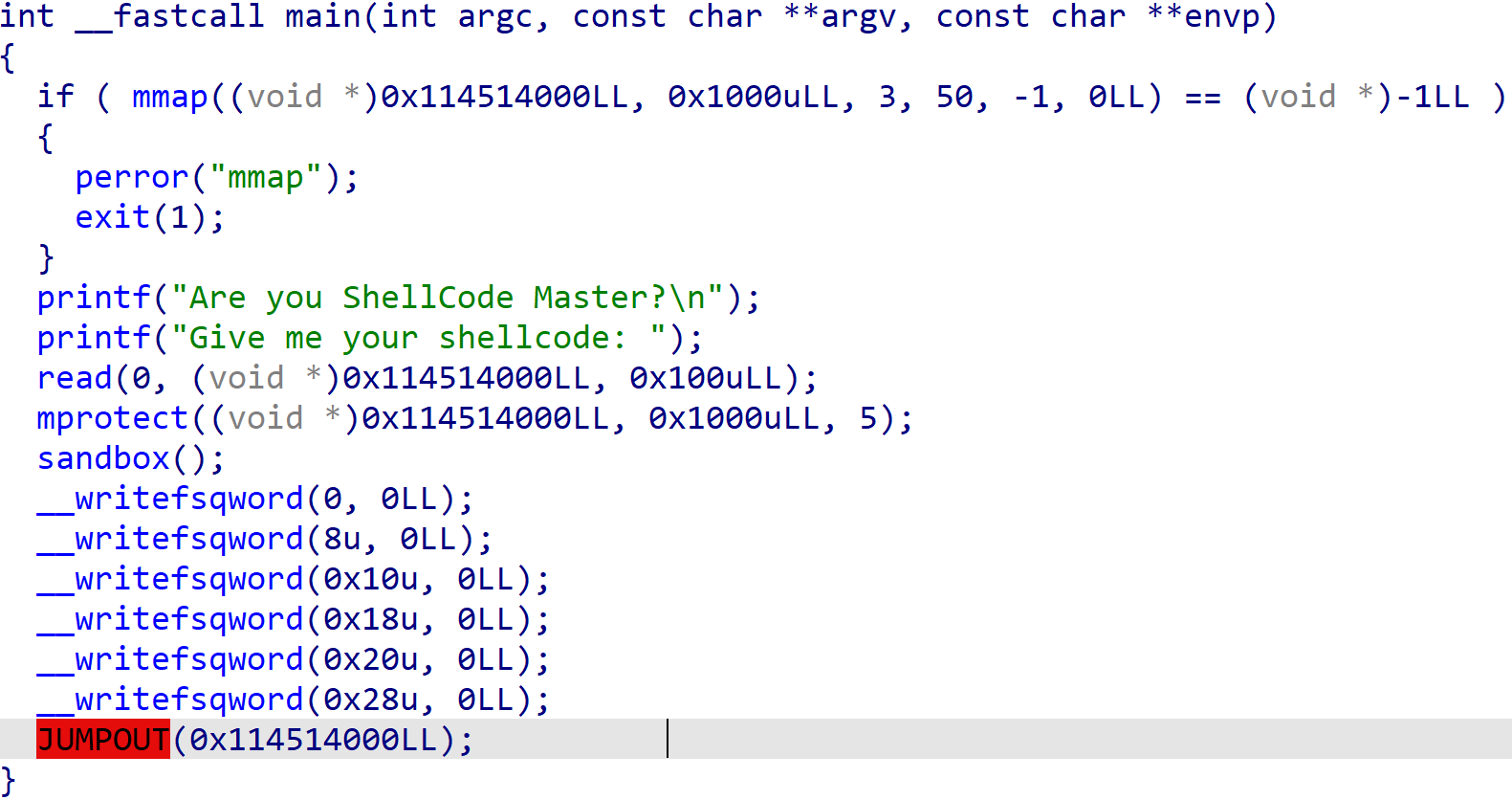
把地址换成了固定的0x114514000,不能把flag写在bss段了(
思路还是一样的,不过这次要利用read读数据到不可写地址时返回负数的原理来爆破找一个可写的地址
1 | |
在原来的exp上又稍微改进了一下,在0x7fffffff000的地址开始爆破
RE
compose
在class3.dex里面找到Main activity和Main activity.kt,可以看出是一个RC4加密,密钥是Tanggegehaoshuai,直接写脚本就爆出来了
1 | |
WEB
1. eateateat
小游戏,没什么好说的,直接看源码就秒了
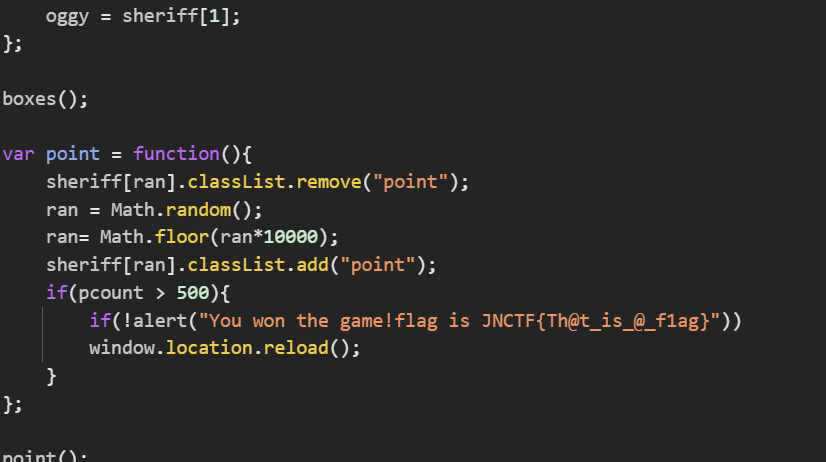
2.test php
先贴源码
1 | |
第三部分可以用md5碰撞,然后给f赋值为system(‘ls -al’)一类的命令来看目录,找到flag后cat一下就好
1 | |
misc
唉,misc就是一坨
1. stego
stego.qoi一个少见的图片格式,去网上找找github的qoi格式转换,把格式换回来就能看见flag
phoboslab/qoi: The “Quite OK Image Format” for fast, lossless image compression
2.ez_pickle_jail
是一个python沙箱,可以利用低版本的pickle数据,这样在反序列后再转序列化就会导致内容不同
1 | |
1 | |
CRYPTO
1.story
给了一大段换表后的文本,这里可以直接就让大语言模型帮忙完成统计爆破
2. 悲伤的故事(有点像misc了)
1 | |
在文本里能看出有栅栏加密(offset=3),base64,维吉尼亚加密。
base64之后:TDRwq@HXcRJr__m11@A{11G___}
栅栏解密:TRADJ{Rr1w_1q_G@m_H1_X1_c@}
根据JNCTF{}的flag格式,可以推断出密钥就是key
最后维吉尼亚解密:JNCTF{Th1s_1s_W@i_J1_N1_y@}
3. 熟悉的故人
源码:
1 | |
RSA,直接脚本秒了
1 | |
后记
没把ezbase打出来可惜了,re也没做出来多少